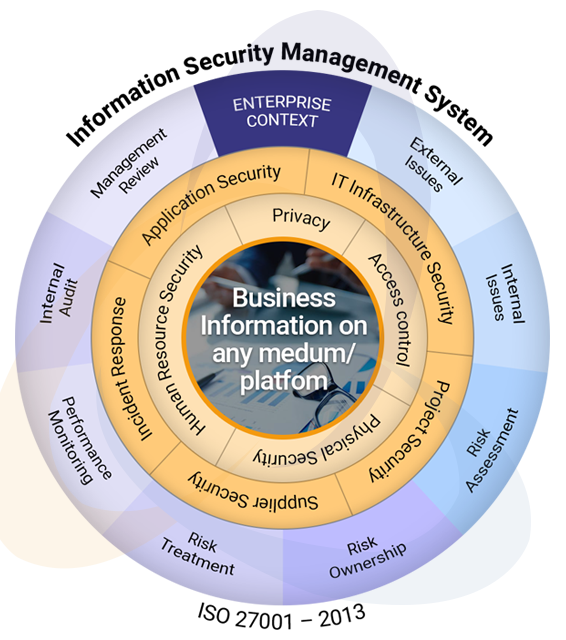
Overview
ISO 27001 aims to protect information in all forms. We have a 7-phase approach that starts with understanding your business first, followed by information security objectives. This is followed by risk assessment and gap analysis - which helps us to recommend and advise you additional security controls. Our risk assessment is one of the most comprehensive assessment that includes all forms of assets that covers technology and non technology infrastructure and processes.
Each ISO 27001 consulting assignment results in transfer of knowledge, documented processes, and a framework that stays with the organisation. We believe in making ISMS simple, articulate, and easy to practice for all stakeholders, thereby gaining ROI on the invested subject.
We have implemented ISO 27001 for 100+ organisations that covered almost all business domains including Banking, Payment Card Processors, Telecom, Insurance, KPO, BPO, Manufacturing, Cloud Services Providers to name a few.
What makes us unique is our involvement in designing your implementation, securing your infrastructure, and reduction of risk. Other unique features involves our project management, our control design framework (5 folder structure per team), our comprehensive documentation, our explanation of each individual control to individual stakeholders, our 3 categories of risk assessment reporting, our 4 dimension tracking, our method of reporting business transactions for security, and ensuring zero defect certification.