Consulting Overview
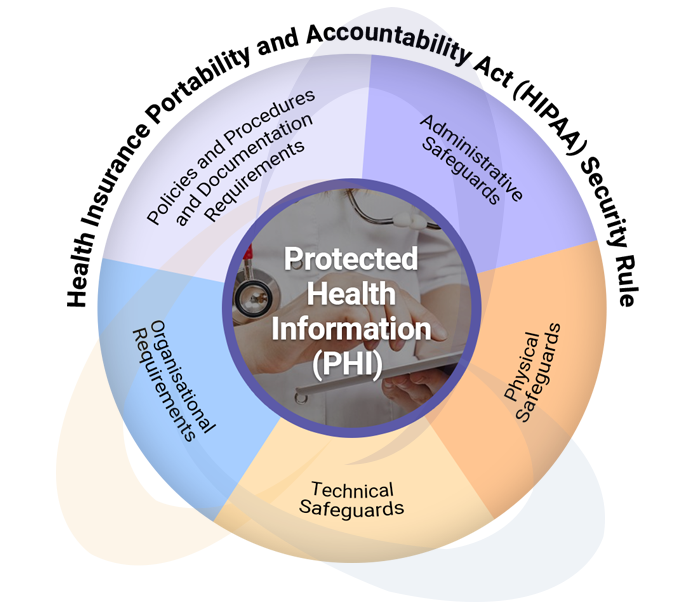
We provide HIPAA consulting and implementation support. This includes identification and assessment of EPHI in the network, risk assessment, vulnerability assessment, detail recommendations, policy/documentation support, gap implementation tracking, training, coaching data protection officers, internal audit, and management review leading to successful HIPAA compliance